Staying ahead of cyber threats is part of our commitment to protecting clients from evolving risks. Recently, we spotted a concerning trend that’s making its way through inboxes and web browsers: malware delivered through fake CAPTCHA prompts.
What’s Happening?
Cybercriminals are leveraging fake CAPTCHA pop-ups to trick users into deploying malware on their own systems. Unlike traditional CAPTCHAs that verify you’re human by having you click images or type distorted text; these malicious versions display a “Verification key CAPTCHA” prompt. The fake CAPTCHA then instructs users to copy a suspicious command, posing as a “verification key,” and run it on their local computer.
Important: No legitimate CAPTCHA will ever ask you to copy and execute a command on your machine. This is a key red flag.
What’s the Risk?
When a user runs the so-called “verification key” locally, they’re often unknowingly installing a remote access trojan (RAT), spyware, and/or additional persistence mechanisms. Once installed, attackers could:
- Gain remote control over a victim’s machine
- Steal sensitive data
- Commit financial fraud
- Execute ransomware
What to Watch For
If you’re wondering, “Should I copy a verification key for CAPTCHA?” the answer is NO. While these instructions may seem harmless enough, if you follow the steps you will actually be infecting yourself with malware, most likely an information stealer. Here are some specific warning signs:
- Be wary of CAPTCHA prompts that ask you to perform actions beyond simple checkbox verification, such as pressing multiple keys or running commands.
- If a website instructs you to paste content from your clipboard into the Run dialog box, it’s likely malicious.
- Messages telling you to copy and paste a code into your system as part of “verification” should not be trusted.
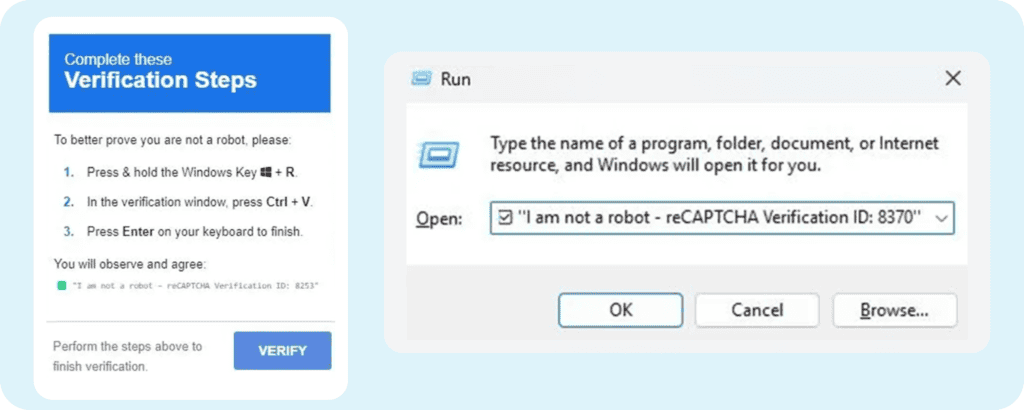
What Should You Do If You Get a Fake CAPTCHA?
- Avoid websites that present the fake CAPTCHA challenge, as shown above in the example.
- Do not copy or run any command suggested by the CAPTCHA.
- Close the tab or browser window immediately.
- Report the incident to your IT team or service provider so they can investigate further.
- Run a malware scan using reputable security software.
- Stay informed—educate yourself and your team about emerging phishing and malware tactics like this one.
Final Thoughts on Fake CAPTCHA Malware
The rise of “Verification key CAPTCHA” attacks is a reminder that cybercriminals are constantly finding new ways to exploit trust and routine behaviors. When in doubt, always verify the legitimacy of prompts before taking any action outside your browser session.
For more information, you can review additional resources like this article from Ohio State University or this post from our MDR partners at Blackpoint.
Have questions or concerns about your organization’s cybersecurity posture? GadellNet is here to help.
