Introduction
In the dynamic landscape of information technology, where digital assets form the backbone of most modern organizations, the importance of IT risk assessments cannot be overstated. These assessments serve as crucial guardians of overall security, playing a proactive role in identifying and mitigating potential vulnerabilities before they can be exploited by malicious actors.
As organizations increasingly rely on interconnected technologies, the need for robust cybersecurity strategies is more important than ever. Performing an IT risk assessment or IT security vulnerability analysis is an important starting point for building these strategies. These foundational tools provide a structured approach to understanding and managing potential risks to your data, your people, and your organization.
This article dives into the significance of an IT risk assessment and its role in cybersecurity. You will learn about the key components of a risk assessment template, examine the benefits of completing one, and review the current trends associated with the overall process. You will walk away with an appreciation for the significant role IT risk assessments play in fortifying the security posture of organizations.
Understanding IT Risk Assessment
IT risk assessment is a systematic process aimed at evaluating potential threats and vulnerabilities within an organization’s information technology infrastructure. It plays a fundamental role in the cybersecurity of an organization by providing insights into potential risks that could compromise the confidentiality, integrity, or availability of data and other digital assets.
The assessment process involves identifying and assessing potential threats to information systems, evaluating the vulnerabilities that could be exploited, and estimating the potential impact of these threats. This systematic examination helps organizations prioritize where to focus and where to implement effective security measures to mitigate the identified risks.
Often, the organization completing the assessment will employ the use of an IT Risk Assessment Template to ensure the evaluation is complete and thorough. A template will provide a framework for a technology-focused audit of systems and processes.

An IT risk assessment is the first integral component of the broader concept of risk management in IT. An organization uses this knowledge to apply resources to minimize or control the impact of these risks. This holistic approach ensures that organizations have a solid foundation from which they will navigate the complex landscape of potential threats effectively.
After completing a thorough risk assessment, an organization is prepared to move forward on its strategic technology roadmap. Leaders will make decisions about everything from cyber liability insurance coverage to mobile device management to cloud vs. on-prem server implementation from a position of deep knowledge.
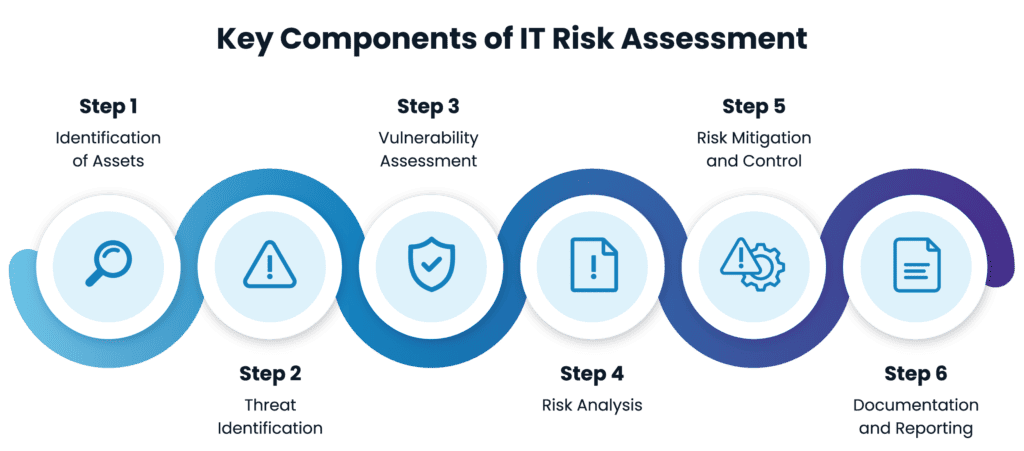
Key Components of IT Risk Assessment
Most IT Risk Assessments have commonalities using a standard operating procedure to efficiently move through all major components. Remember, some vulnerabilities may be small and feel insignificant. Moving through an evaluation process systemically will ensure your organization isn’t missing a small vulnerability that could lead to a large issue. Many assessments involve four major components—identification, evaluation, analysis, and results reporting. Each component can have multiple layers as outlined below.
Identification of Assets: Involves cataloging and understanding the organization’s technology assets, including hardware, software, data, and intellectual property. Not only will this process aid in risk assessment, but it also aids your organization in evaluating its current technology investments. It is a valuable tool not only for risk assessment but for creating a technology strategic roadmap.
Threat Identification: Encompasses the identification of potential threats that could exploit vulnerabilities in the organization’s IT systems. This component helps in understanding the landscape of potential risks that are unique to your organization. A risk assessment template aids in evaluating the types of threats that your organization is most likely to encounter.
Vulnerability Assessment: Focuses on evaluating the weaknesses and vulnerabilities within the organization’s IT infrastructure. This step is crucial for understanding the potential entry points for threats. Cybersecurity infrastructure has three pillars to consider – people, process, and platform. A security vulnerability assessment helps you evaluate each pillar individually so you can determine where improvements may need to be made.
Risk Analysis: Involves the evaluation of the identified threats, vulnerabilities, and the potential impact of a security incident. This analysis helps the organization see all the potential risks and then aids in prioritizing those risks based on their severity.
Risk Mitigation and Control: Encompasses the development and implementation of strategies to mitigate or control the identified risks. This includes the establishment of security controls and measures to reduce the likelihood and impact of potential incidents. Using an assessment template also aids in prioritizing the measures the organization will take and creating a timeline so the organization can move swiftly yet responsibly.
Documentation and Reporting: Involves the documentation of the entire risk assessment process and the preparation of comprehensive reports. This component aids in communication, decision-making, and ongoing risk management. This step also sets the foundation for assessing potential risks to these assets and provides thorough documentation. Complete documentation is important and will be used for efficient planning, effective threat response, and ongoing compliance support.
Benefits of IT Risk Assessment
There are many important benefits to completing an IT risk assessment. Most, if not more, would have an impact on your organization’s planning and overall security posture.
Identifying and Mitigating Risks Proactively: Conducting periodic IT risk assessments allows organizations to identify and mitigate potential threats and vulnerabilities before incidents occur. The assessment helps an organization better understand the risk landscape and therefore, they can implement safeguards, improvements, and other measures to enhance their cybersecurity posture.
Contributing to Proactive Cybersecurity Measures: Not only will an IT risk assessment help an organization identify potential risks but learning about potential vulnerabilities can contribute significantly to the development of ongoing proactive cybersecurity measures. By identifying and addressing risks before they materialize into security incidents, organizations can stay ahead of potential threats, protecting their digital assets effectively.
Improved Incident Response Preparedness: By understanding potential risks and vulnerabilities, organizations can enhance their incident response preparedness. IT vulnerability assessments provide a roadmap for responding to security incidents effectively, minimizing the impact and downtime associated with breaches.
Enhancing Business Continuity Planning: IT risk assessments play a crucial role in responding to an event but also in crafting a business continuity plan. By identifying and mitigating potential risks to people, platforms, and processes, organizations ensure the resilience of their operations, minimizing disruptions and ensuring continuity even in the face of unforeseen events. A business continuity plan built with assessment results in mind allows each of your organization’s leaders to react quickly and cohesively to a business interruption.
Meeting Regulatory Compliance Requirements: Risk assessments are instrumental in meeting regulatory compliance requirements. Many regulatory frameworks, such as GDPR and HIPAA, mandate organizations to assess and manage risks to safeguard sensitive information. Compliance with these regulations is crucial for avoiding legal repercussions and maintaining trust.
In addition, many cyber liability insurance plans have many requirements to be met before coverage can be provided. An IT security vulnerability analysis, though not necessarily mandatory, can make the renewal process more efficient.
Enhanced Decision-Making: The insights gained from IT risk assessments empower organizations with data-driven decision-making. Leaders can make informed choices regarding resource allocation, security investments, and strategic planning to address potential risks effectively.

Conducting an Effective IT Risk Assessment
Conducting an effective IT risk assessment involves a systematic process. The assessment process begins by identifying and cataloging digital assets, followed by a thorough analysis of potential threats and vulnerabilities. Then, evaluate the likelihood and impact of each risk, prioritize them based on severity, and develop strategies for mitigation. After that, organizations must regularly review and update the risk assessment to adapt to evolving threats.
There are two main methodologies employed when performing an IT risk assessment. Quantitative methodologies involve assigning numerical values to risks and as a result, return an objective and detailed measure of potential impact. However, quantitative assessment is dependent upon access to enough curated data to perform the analysis.
Qualitative methodologies, on the other hand, use descriptive terms to assess risks. Qualitative risk analysis can be used on most business functions quickly. However, qualitative analysis will also be at risk of bias or the lack of experience of those team members participating.
Most commonly, a combined approach is used and results in a thorough and efficient return of information. However, understanding these methodologies enables organizations to choose the most suitable approach based on their specific needs.
Whichever methodology is employed, it is important to emphasize the collaborative risk evaluation involving key stakeholders. The assessment should engage with individuals from different departments, including IT, legal, compliance, and business units, to provide diverse perspectives on potential risks. This collaborative approach ensures a more comprehensive and accurate risk assessment, incorporating insights from various domains within the organization.
A thorough assessment will leverage specialized risk assessment tools and software to streamline the process. These tools often include features for asset identification, risk analysis, and reporting. Integration of technology can enhance the efficiency and accuracy of the risk assessment process.
One important tool is the IT security audit. IT security audits complement risk assessments by providing a comprehensive examination of an organization’s security controls and practices. Audits help verify the effectiveness of existing security measures and identify areas for improvement. They play a crucial role in validating the accuracy of risk assessments and ensuring that the implemented controls align with industry best practices.
IT risk assessment is an event, but it requires continuous monitoring and adaptation throughout the process. The threat landscape is dynamic, and organizations must regularly reassess and adapt their risk assessments to stay ahead of emerging risks. This involves periodic reviews, updates, and collaboration with stakeholders to ensure ongoing effectiveness.

Trends in IT Risk Assessment
Focus on Cloud Security Risks: With the widespread adoption of cloud services, there is a growing emphasis on assessing and managing risks associated with cloud environments. IT risk assessments are evolving to address unique challenges related to cloud security, such as data protection, identity management, and shared responsibility models.
Quantification of Cyber Risk: There is a trend towards quantifying cyber risk in financial terms. Organizations are seeking to express cybersecurity risks in monetary value, enabling better communication with business stakeholders. This approach facilitates informed decision-making regarding risk mitigation investments like right-sizing cyber liability coverage.
Regulatory Compliance Evolution: As regulatory frameworks evolve, there is an increasing focus on incorporating regulatory compliance requirements into IT risk assessments. Organizations are aligning risk assessment processes with the changing regulatory landscape to ensure continuous compliance and reduce legal and financial risks.
Enhanced Automation in Risk Assessment Processes: Automation is becoming more prevalent in conducting risk assessments. Automated tools can streamline data collection, analysis, and reporting, allowing organizations to perform more frequent risk assessments. This trend is expected to improve efficiency and ensure assessments are conducted in near real-time.
To further enhance the accuracy and speed of risk assessments, organizations are increasingly using the integration of AI-driven (Artificial Intelligence) tools to analyze vast amounts of data, identify patterns, and predict potential risks more efficiently than traditional methods.
Advanced Threat Intelligence: IT risk assessments are increasingly leveraging advanced threat intelligence sources. Continuous monitoring of global threat landscapes and understanding the tactics, techniques, and procedures employed by cyber adversaries provide organizations with real-time insights to enhance their risk assessment strategies.
In the ever-evolving information technology landscape, IT risk assessments play a proactive role in identifying vulnerabilities and mitigating potential threats to organizations of all sizes and industries. IT risk assessments have several major components that emphasize their importance in fortifying organizational security postures. Completing a thorough assessment of your organization will have benefits ranging from proactive risk mitigation to improved incident response preparedness and enhanced business continuity planning.
In addition, IT risk assessments will continue to be an increasingly important part of strategic technology planning. Many emerging trends, including a focus on cloud security, compliance, and increased automation through AI-driven tools, will drive organizations to use an assessment as a foundational tool for security and productivity. In essence, IT risk assessments are indispensable tools that empower organizations to navigate the future with resilience and strategic agility.
If you’d like to learn more about IT risk assessment services and how GadellNet can get your organization started toward securing your IT infrastructure, contact us today for personalized guidance.