Introduction to MSSP
An MSSP, meaning Managed Security Service Provider, is an outsourced cybersecurity provider. MSSPs offer cybersecurity monitoring and cyber threat response. MSSPs have emerged as pivotal allies for organizations in the ever-evolving cybersecurity landscape. In a digital age characterized by sophisticated threats and complex regulatory environments, organizations turn to MSSPs to fortify their defenses and safeguard sensitive information. These specialized outsourced providers offer a comprehensive suite of security services, from threat detection and incident response to vulnerability management and compliance monitoring.
What is an MSSP? At their core, MSSPs are responsible for proactively managing and enhancing an organization’s security posture. MSSPs empower businesses to focus on their core operations as they’ve offloaded cybersecurity. Organizations entrust intricate cybersecurity management tasks to these specialized professionals who leverage cutting-edge technologies and hold a deep reservoir of cybersecurity expertise. This approach bolsters an organization’s resilience and provides a cost-effective alternative to maintaining an in-house cybersecurity infrastructure.
As the threat landscape evolves, MSSPs play a crucial role in staying ahead of cybersecurity threats. Their ability to deliver real-time threat intelligence, continuous monitoring, and rapid response capabilities positions them as vital partners in the ongoing battle against cyber threats.
This article answers what an MSSP is, the benefits of using an MSSP, an MSSP’s important role in an organization’s cybersecurity posture, the key services offered by MSSPs, how to choose the right MSSP partner, and MSSP industry trends and innovations.
What Is MSSP?
MSSP means Managed Security Service Provider. These third-party organizations offer outsourced management of an organization’s security infrastructure and services. MSSPs are instrumental in fortifying cybersecurity defenses through outsourced management of an organization’s security infrastructure and services. With a dedicated staff and cutting-edge technology stack, MSSPs offer a comprehensive suite of cybersecurity services encompassing continuous monitoring, threat intelligence, and vulnerability management. This proactive approach is crucial in safeguarding organizations against the ever-evolving threat landscape.
Outsourcing cybersecurity to MSSPs allows businesses to access cost-effective solutions without requiring substantial investment in specialized personnel and technology. A complete in-house cybersecurity team demands multiple skilled members with sizeable salaries and a full technology stack. In contrast, MSSPs bring scalability and flexibility to cybersecurity operations, adapting to each client’s unique requirements.
MSSPs, at their core, are external partners responsible for safeguarding an organization against cyber threats. They specialize in overseeing and managing an organization’s security infrastructure, offering a comprehensive suite of cybersecurity services.
The technology and expertise of MSSPs empower them to stay ahead of cyber threats, offering dynamic protection. Considering the potential costs, time consumption, and vulnerability of cyber incidents, this proactive stance is essential. MSSPs can stay proactive and detect threats before they become an issue through advanced monitoring, which is part of their sophisticated technology stack. Monitoring and proactive threat detection ensure their clients minimize potential damage from a cyberattack and maintain their reputation. Customers’ sensitive data, a prime target for cybercriminals, is a top priority for MSSPs’ proactive protection. MSSPs are essential in creating a cybersecurity base in organizations by combining continuous monitoring, threat intelligence, and vulnerability management, providing a holistic and proactive cybersecurity strategy.
Benefits of Using an MSSP
MSSPs offer a range of benefits. Their expertise and specialized knowledge are foundational to the benefits they bring an organization. MSSPs employ individuals well-versed in the latest threats, vulnerabilities, and security best practices. It is a top priority for MSSPs to continually educate their employees and stay up to date on the latest technologies and threats. These investments save their clients time and money.
An organization’s security posture is enhanced when partnered with an MSSP through many of the key services offered by an MSSP. Additionally, an organization can offload an in-house cyber team’s financial and time burden.
MSSPs offer around-the-clock protection, another key benefit. This protection would include security monitoring, threat detection, incident response, and foundational cybersecurity practices.
Security Monitoring
MSSPs continuously monitor an organization’s networks, systems, and applications. This continuous monitoring involves analyzing logs, events, and traffic patterns to detect unusual activity, which could indicate a threat.
Threat Detection
MSSPs use advanced technologies and threat intelligence to detect and identify potential cybersecurity threats. The proactive approach allows for early detection of malicious activities before they can escalate into security incidents.
Incident Response
In the event of a cybersecurity incident, MSSPs provide incident response services, including investigation, containment, and eradication of threats and recovery efforts to minimize the impact of an incident.
When to Use MSSP Services
Resource Constraints
Organizations with limited resources, including budget and skilled personnel, may benefit from outsourcing security services to an MSSP to ensure robust protection.
Increasing Cyber Threats
In the face of a rising number of sophisticated threats, organizations may turn to MSSPs to strengthen their defenses and keep pace with evolving attacks.
Compliance Requirements
Industries with stringent regulatory requirements may be interested in leveraging MSSP services to ensure compliance with security standards and frameworks.
Need for Proactive Defense
Organizations looking to adopt a proactive cybersecurity stance, including early threat detection and continuous monitoring, find MSSPs valuable in enhancing their security posture.
Why MSSPs Matter in Cybersecurity
MSSPs play a crucial role in strengthening an organization’s cybersecurity posture, especially in the face of an evolving threat landscape. Threats are multifaceted and ever-evolving. MSSPs offer organizations a strategic advantage with their specialized knowledge, proactive defense measures, and continuous monitoring. The robust cybersecurity solutions offered by MSSPs empower organizations to focus on their core operations while maintaining a resilient and adaptive security posture.
Strengthening Cybersecurity Posture
MSSPs provide specialized expertise and services to enhance an organization’s security strategy. By outsourcing security functions to MSSPs, organizations can access various advanced cybersecurity services, including threat detection, incident response, and vulnerability management. MSSPs bring a depth of knowledge and experience, helping organizations navigate the complexities of modern cybersecurity challenges.
Evolving Threat Landscape
The cybersecurity landscape is dynamic, with cyber threats evolving in sophistication and complexity. MSSPs stay updated on the latest threat intelligence, emerging attack trends, and vulnerabilities. This continuous monitoring allows them to adapt their security measures proactively. MSSPs leverage cutting-edge technologies and employ skilled cybersecurity professionals to stay ahead of cyber adversaries, providing real-time defense against new and emerging threats.
Evolving Threat Landscape
The cybersecurity landscape is dynamic, with cyber threats evolving in sophistication and complexity. MSSPs stay updated on the latest threat intelligence, emerging attack trends, and vulnerabilities. This continuous monitoring allows them to adapt their security measures proactively. MSSPs leverage cutting-edge technologies and employ skilled cybersecurity professionals to stay ahead of cyber adversaries, providing real-time defense against new and emerging threats.
Impact on Preventing Security Breaches
Threat actors, who are responsible for cyber threats, often perceive small- and medium-sized businesses as easy targets, according to Blackpoint Cyber. Forty-three percent of cyber attacks target small businesses (SMBs), but only 14% of these SMBs have the cybersecurity in place to counter these threats. Because of this, 60% of SMBs targeted by a cyberattack fail within six months, according to Verizon. These SMBs go under as a direct result of their cybersecurity readiness. Mitigating security breaches can have a direct impact on the success of SMBs.
Key Services Offered by MSSPs
MSSPs offer a range of services to organizations. As discussed, these services all work together to protect organizations from cyber threats. Full protection requires a layered approach because of the highly sophisticated nature of cybersecurity and cyber threats. This layered approach requires more than a technology stack, it also includes the people who interact with the environment, who require training, and the processes put into place by the MSSP and the organization.
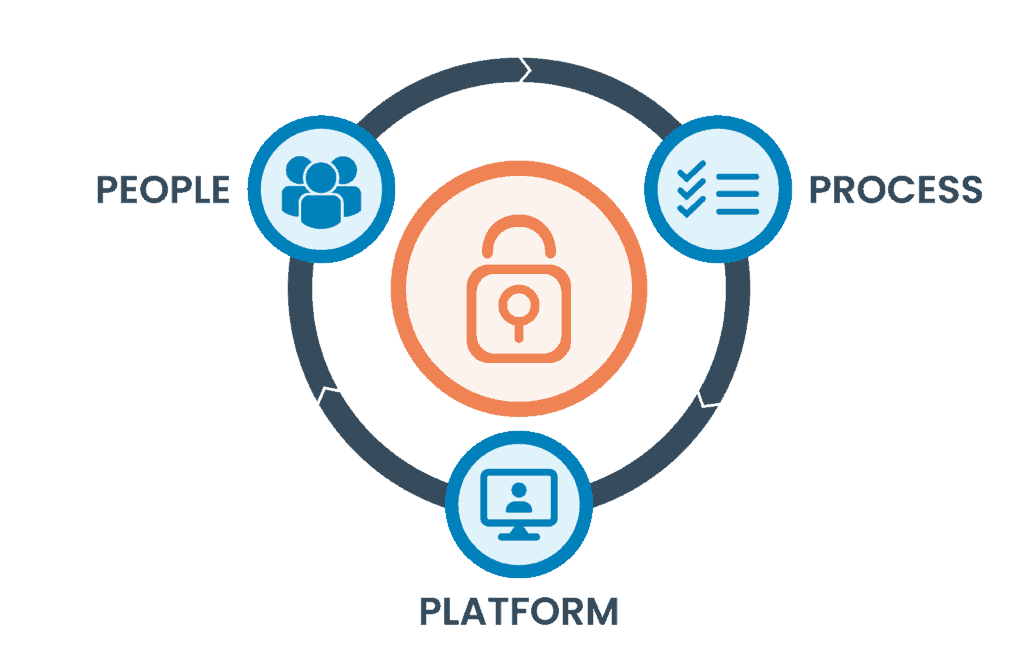
Here are key services provided by MSSPs:
1. Network Security is a set of measures and practices designed to protect the integrity and confidentiality of computer networking. Network security exists to prevent unauthorized access, data breaches, and other cyber threats that can compromise the functionality and security of a network. Network security includes firewalls, intrusion detection and prevention systems, virtual private networks, authentication and authorization, patch management, security audits, encryption, network access controls, and more. The importance of network security cannot be understated. It requires a comprehensive and layered approach, considering internal and external threats.
2. Endpoint Protection safeguards the various endpoints in a network, such as individuals’ devices, from cyber threats. These individual devices that connect to the network, such as desktops, laptops, servers, smartphones, and more, possess data that needs to be protected and, in many cases, are driven by individuals who could fall victim to cyber-attacks, such as phishing schemes. Endpoint protection secures these devices and the data they access, store, and transmit against various malicious activities and cybersecurity risks.
3. Threat Intelligence brings together information and analysis about potential cyber threats, vulnerabilities, and risks that may harm an organization’s information systems, networks, or data. Threat intelligence is the informed decision-making piece of cybersecurity offered by MSSPs. It is a crucial component of cybersecurity, empowering organizations to enhance their security posture and proactively defend against cyber threats with the information gathered. Threat intelligence encompasses data collected from various sources, which is then processed, analyzed, and disseminated to help MSSPs understand and respond to potential cyber threats effectively.
4. 24/7 Monitoring and Response is a critical component of a proactive cybersecurity suite. Cyber threats can emerge anytime, day or night. MSSPs employ sophisticated tools and technologies to monitor network activity, identify abnormalities, and respond swiftly to potential security threats. This constant vigilance enables organizations to detect and counteract cyber threats effectively, thereby mitigating the impact of cyber-attacks and ensuring the resilience of their digital infrastructure.
5. Security Information and Event Management (SIEM) products manage and analyze security information and events within an organization’s IT infrastructure. SIEM systems collect and aggregate log data generated through the organization’s technology infrastructure, from host systems and applications to network and security devices such as firewalls and antivirus filters. The primary purpose of SIEM is to provide a centralized platform for real-time analysis of security alerts generated by various hardware and software applications. Important parts of SIEM are normalization and real-time monitoring to alert for out-of-the-ordinary events which could indicate a cyber threat.
6. Incident Response and Investigation focus on effectively managing and mitigating security incidents when they occur. When any threatening adverse events or violations of security policies occur, incident response and investigation seek to identify the root cause and prevent similar incidents in the future.
7. Vulnerability Management is a proactive approach to identifying, assessing, prioritizing, and mitigating security vulnerabilities in an organization’s information systems, networks, and applications. Vulnerability management aims to reduce the risk of security breaches by addressing potential weaknesses that hackers could exploit. This is an important piece of an MSSP’s proactive approach to cybersecurity. This process involved a systematic and continuous cycle of discovery, assessment, and remediation of vulnerabilities to enhance the overall security posture of an organization.
8. Compliance Management involves ensuring an organization adheres to industry regulations, legal requirements, and cybersecurity standards to ensure its security practices meet the necessary criteria. Compliance management is particularly crucial in finance, construction, healthcare, and government industries, where regulatory compliance is stringent, and non-compliance can result in severe consequences. An MSSP can help an organization navigate changes in these regulations as they arise.
9. Risk Assessment and Mitigation are part of managing and reducing the impact of potential threats and vulnerabilities on an organization’s information systems and data. An MSSP identifies, analyzes, and prioritizes risks and then implements strategies to minimize or eliminate those risks.
10. Security Awareness Training is a key piece of a layered cybersecurity approach that addresses the risk of human error. Security awareness training is focused on end-user education to ensure each employee can identify a potential threat and not fall victim to common cyber threats, such as phishing emails or social engineering. It is important to make security awareness training ongoing as new threats and technologies emerge. Keeping individuals informed and vigilant is essential to an organization’s cybersecurity posture.
Case Study
GadellNet’s partner, Blackpoint Cyber, lays out a real-life example of how increased response time minimized the impact of a cyberattack.
5:14 am EST – Receive an alert “Login from New Device and IP.” The location, Netherlands, was labeled risky.
5:21 am EST – Receive an alert “Login from New Device and IP.” The location, Nigeria, was labeled risky.
5:23 am EST – A SOC (Security Operations Center) analyst escalates the ticket after reviewing both alerts for unapproved logins.
5:23 am EST – A Sr. SOC analyst reviews the escalation.
5:28 am EST – The Sr. SOC analyst disables the M365 user account, reaches out to the organization on the emergency contact line, and begins working on the incident response report.
7:34 am EST – The Sr. SOC analyst sends the incident response report to the partner.
8:00 am EST – The client opens for business.
8:30 am EST – The MSP contacted the affected client’s points of contact and started the process to get the affected user back into their accounts and confirm that the threat had been eliminated.
9:15 am EST – The affected user was back up and running securely.
The entire process, from the suspicious login attempt to shutting down the compromised account, took 14 minutes and the impact on productivity was minimized.
For more details, check out this article.

Choosing the Right MSSP Partner
Once an organization has established that it needs to outsource its security needs, it is time to choose the right MSSP partner. An organization should partner with an MSSP that is a cultural fit, a fit for their industry and has the experience to help the organization stay protected.
Here are a few questions to as an MSSP you’re considering partnering with:
1. Can you provide details about your team’s experience and qualifications, including any certifications?
2. Can you customize cybersecurity services based on our organization’s unique needs?
3. Do your services and technology stack include a comprehensive offering from threat detection, incident response, and vulnerability management?
4. How do you stay up-to-date on the latest cybersecurity trends, threats, and technologies?
5. How quickly can you respond to a security incident?
6. How scalable are your services to accommodate our organization’s growth?
7. Will you provide a clear breakdown of the pricing structure?
8. Do you have partnerships with third-party cybersecurity vendors or organizations?
9. Can you share the performance metrics you use to measure your own effectiveness?
10. Do you offer security awareness and training for employees?
MSSP Industry Trends and Innovations
MSSPs have always had to stay nimble due to the nature of cyber threats. In a trend-dominated industry, MSSPs work to align their services with the needs of the day. MSSPs are required to stay proactive, efficient, and adaptable. MSSPs provide clients with advanced security measures and tailored solutions to align with the latest industry best practices.
The ever-evolving threat landscape leads MSSPs to leverage innovative technologies to continue to stay ahead of threats.
Here are a few key MSSP industry trends:
- Cloud Security Integration
As organizations increasingly migrate to cloud environments, MSSPs adapting their services to secure cloud infrastructures effectively. Providing cloud-native security solutions, managing cloud access, and protecting data stored and processed in the cloud are all part of cloud security integration.
- Threat Hunting Capabilities
MSSPs are placing a greater emphasis on proactive threat hunting. Threat hunting identifies and mitigates potential risks before they escalate. Through advanced analytics, threat intelligence, and behavior analysis, MSSPs enhance their detection capabilities and stay ahead of sophisticated cyber threats.
- Automation and Orchestration
Integrating automation and orchestration streamlines MSSP operations. Automated responses to common security incidents, coupled with orchestrated workflows, enable MSSPs to enhance efficiency, reduce response times, and focus their human resources on more complex security challenges.
- Artificial Intelligence and Machine Learning
Artificial Intelligence (AI) and Machine Learning (ML) play a larger role in threat detection and analysis within MSSPs. These technologies enable MSSPs to analyze vast amounts of data, identify patterns, and detect anomalies that might indicate potential security threats, contributing to more accurate and rapid threat identification.
- Zero Trust Security Models
MSSPs adopt Zero Trust security models as cyber threats grow in sophistication. In Zero Trust, the assumption is that no entity from inside or outside the organization is trustworthy. MSSPs implement stringent access controls and continuous authentication to enhance overall security posture.
- IoT Security
As the Internet of Things (IoT) ecosystem expands, MSSPs focus on IoT security. Protecting interconnected devices and networks from potential vulnerabilities and ensuring the integrity of IoT data are becoming integral components of MSSP offerings.
- Continuous Compliance
The MSSP industry is placing increased emphasis on helping organizations maintain continuous compliance with evolving regulations. MSSPs align their services with industry-specific compliance requirements, providing clients with the necessary tools and processes to adhere to changing regulatory landscapes.
Conclusion
MSSPs are an essential partner for many organizations looking to fortify their cybersecurity defense without adding an in-house team. MSSPs bring a depth of knowledge and a technology stack that cannot be rivaled. With the cybersecurity landscape evolving as quickly as it always has, partnering with a dedicated team can prove to be make or break for organizations.
At GadellNet, we employ a team of highly skilled and trained cybersecurity experts. Coupled with our technology stack, we can offer our clients the full gambit of cybersecurity services. We additionally offer cybersecurity consulting, ensuring technology roadmaps will align with organizations’ core responsibilities and see organizations well into their futures.
